Enterprise
IT Solutions
Enterprise Applications & Integrations
Enterprise applications are business oriented and deployed to meet specific business requirements that can work on large chunks of data, extensive parallel processing, network distributed resources and complex logic. Integration is focused on optimizing operations in a real world which could be considered full of continuous and largely unpredictable change. It enables the actors to make “quick and accurate decisions and adaptation of operations to respond to emerging threats and opportunities”
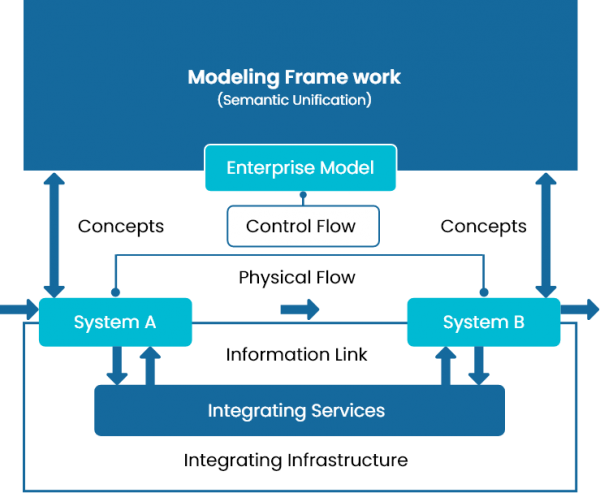
A concept in enterprise engineering to provide the right information at the right place and at the right time and thereby enable communication between people, machines and computers and their efficient co-operation and co-ordination.
Enterprises are entering the age of the connected customer. Today, an enterprise’s connections with their customers and employees offer enormous value from streams of real-time data — the data that can be unlocked with apps. But for Enterprise IT, those charged with building these apps, this means they need to adopt a new approach to enterprise application development.

New and Emerging trends in Enterprise Application & Integration is impacting application development in a big way. Some of the key trends are:
- Small, emerging businesses are increasingly expected to trade with their customers electronically – exchanging key business documents such as orders and invoices via EDI
- Cloud computing has increased accessibility and ease of operation for users of Enterprise application development.
- Loose Coupling (Microservices, Composable architecture)
- Integrated Enterprise Information & Identity Management
- Support for disruptive innovations
- Ecosystem that accelerates innovation
- Low code development is the new trend in Enterprise. Minimal Coding is making Enterprise Application Development more business centric and easy.
What we do?
- Identify and provide the right information at the right place in right time
- Coordinate business processes with API-led integration
- Deep EDI Integration with your ERP
- Organize and adapt the enterprise
- Automate User Provisioning, Deprovisioning, enable Advanced Directory Integration, Single Sign On using standard protocols, and multi-factor authentication
- Provide capabilities to consolidate master data from heterogeneous sources into a centralised repository and manage it.
- Establish a technology-independent vocabulary and a visual notation to design and document integration solutions, ranging from connecting applications to a messaging system, routing messages to the proper destination, and monitoring the health of a messaging system using Enterprise Integration Patterns (EIPs)
Application Modernization
Application modernization aims to retain and extend the value of the legacy investment through migration to new platforms. Legacy systems are often critical in the operations of most enterprises, deploying the modernized system all at once introduces an unacceptable level of operational risk. A migration strategy must ensure that the system remains fully functional during the modernization effort.
We mainly see lack of documentation, lack of SMEs/ knowledge on the legacy systems and dearth of technology skills in which the legacy systems have been implemented as primary issues with a legacy system.


What we do?
- Initiate Architecture Driven Modernization (ADM) to standardize views of the existing systems
- Prepare methods for iteratively evaluating legacy systems, from technical, business, and organizational perspectives (Application Portfolio Management)
- Follow Migration, Re-engineering, or Package Implementation options based on analysis
- Define potential problems in reengineering and its mitigation strategy (Both Technology and Business Objectives)
- Follow component-based software development to enhance productivity and accelerate time to market
- Design and implement Microservice architecture style applications
- Automate business operations using Robotic Process Automation
Enterprise Information Management
The explosion of information sources and integration challenges, together with greater regulation and compliance requirements have created new challenges for today’s enterprise Information solutions.
Finding solutions for optimal use of information within organizations, for instance to support decision-making processes or day-to-day operations requires the availability of knowledge by managing information at enterprise level.
It is now a need to maximize the potential of the digital information framework with the Extended Enterprise Content Management application. Manage documents and records, information retrieval, and collaboration. Connect e-mails, presentation slides, documents, and other unstructured content to core business processes. Consolidate and centrally govern the master data lifecycle to increase the quality and consistency of information across your organization is vital.


What we do?
- Guide, Design, and Implement document management, Web content management, search, collaboration, records management, digital asset management (DAM), workflow management, and data indexing.
- Enterprise content management as a uniform repository for all types of information
- Use various recognition technologies to extract information from scanned documents and digital faxes including OCR, and ICR
- We use template-driven web design techniques and probe into your organizational requirements
- Provide capabilities to consolidate master data from heterogeneous sources into a centralized repository and manage it.
- Establishing policies and processes that ensure information can be integrated, accessed, shared, linked, analyzed and maintained to best effect across the organization.
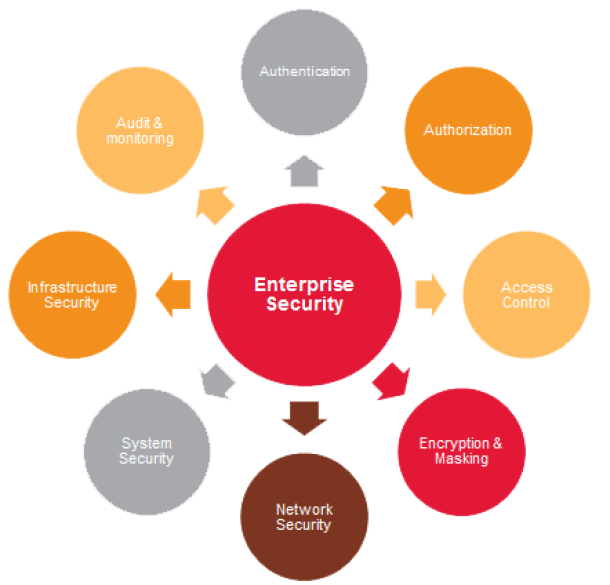
Enterprise Security
- Network Security – Servers, Databases, APIs Security, Application Security. Needs Security Engineering, Vulenrability Testing, Penetration Testing, Network Intrusion Detection Systems (NIDS) and Firewalls.
- Internet Security – TLS/SSL
- Cloud Security – Web sockets, Auth protocols
- Wireless Security
- Endpoint Security – Computer, Mobile, Email – VPN, Encryptions
- Information Security – Protection of our data

Security assurance is the foundation enterprises need to build for determining trustworthiness of features, practices, processes, procedures and architecture of the information system. Security assurance services assist clients across a wide range of industry verticals in determining the compliance level of the technical security controls with applicable regulations, legislative and standard requirements such as PCI DSS, UK DPA, HIPAA and ISO 27001.
What we do?
- Define, implement, and measure a software security initiative (SSI)
- Suggest & Implement relevant application security lessons based on CWEs
- Provide data protection services through audits, threat analysis, and risk assessments
- Implement Cloud Security Maturity Action Plan
- Follow Security Coding Guidelines
- Application Security Testing Services such as Penetration Testing, DAST, SAST, and Mobile Application Security Testing to address your unique testing requirements and risk profile.
- Governance: ITIL; CoBIT, ISO/IEC 20000, ISO/IEC 27000, IS Governance
- Digital / Process transformation, IS Risk Management, Security Operations
- Identify flaws within system designs to improve your security posture
- Accelerate your application security program
- Test for vulnerabilities in a resource-constrained environment using open source techniques
- Implement SIEM for your enterprise if needed
Case Studies
Enterprise Solutions
Automates the ordering process through systems integration, reduces manual work and provides current data to validate order information with visibility into all orders being placed.
We involved in providing cloud based exchange platform and services to help supply chain customers efficiently automate their order process. AWS was leveraged heavily for make this solution highly available for any number of partners. We have involved in setting up Master Data Management aligned with Single Login option for their customers. Our managed EDI service helps in processing complex EDI transformation that reaches this system using efficient EDI tools and techniques.
Healthcare Master Data
Single source of master data to productize customer lookup, item lookup and transaction intelligence. Providing a way for internal and external systems to make use of this data securely.
We designed and implemented master data management, a secured data governance model with quality control and efficient source error correction techniques. Involved in design and implementation of APIs to migrate any new applications to the system.
Enterprise and Federated Identity Management
Provides enterprise and federated identity management for internal and their customers to seamlessly access supply chain solutions.
We analysed, designed and implemented a protocol that suites open standard security to provide enterprise and federated identity management solution. Implementation also covers multi factor authentication and attribute based authorization for their services using PIP (Policy Information Point), PDP (Policy Decision Point), and PAP (Policy Administration Point).
Security Information and Event Management
Collect logs, analysis on logs, correlate events, ensure IT compliance, user activity monitoring, real time alerting and object access auditing.
We involved in technology selection with their DevSecOps team to implement SIEM providing all above security governance to internal and external applications.
Credentialing Service
Service that will make sure supplier representatives are ready compliance with the industry-driven requirements of their healthcare customers, they are not only sales ready, but also considered valued partners.
We developed a framework that suites SOA based architecture style and efficient usability interface. We did analysis of the existing system starting from design and provided the customer a strategic path to integrate our framework. We also defined the approach to evaluate the application improvements from the customer experience perspective againsts their business goals.
Technology we play with























